Dump | demo: Dump Test Engine Demo miễn phí
HOTSPOT
-
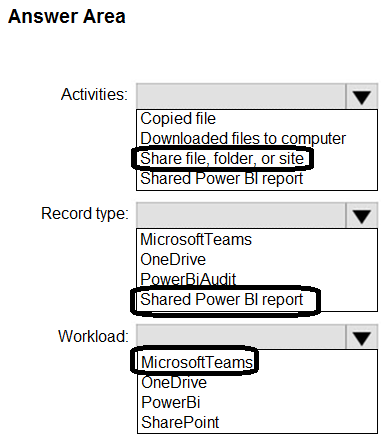
You have a Microsoft 365 E5 subscription that uses Microsoft Purview and contains a user named User1.
User1 shares a Microsoft Power BI report file from the Microsoft OneDrive folder of your company to an external user by using Microsoft Teams.
You need to identify which Power BI report file was shared.
How should you configure the search? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.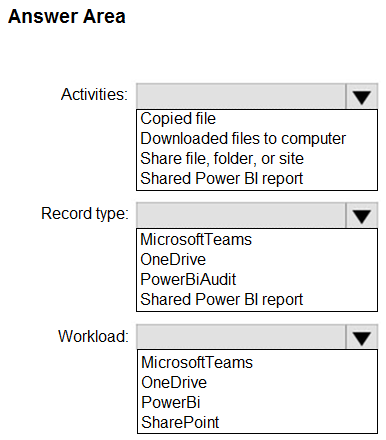
DRAG DROP
-
Case study
-
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
-
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
-
Litware Inc. is a renewable energy company.
Litware has offices in Boston and Seattle. Litware also has remote users located across the United States. To access Litware resources, including cloud resources, the remote users establish a VPN connection to either office.
Existing Environment
-
Identity Environment
-
The network contains an Active Directory forest named litware.com that syncs to an Azure Active Directory (Azure AD) tenant named litware.com.
Microsoft 365 Environment
-
Litware has a Microsoft 365 E5 subscription linked to the litware.com Azure AD tenant. Microsoft Defender for Endpoint is deployed to all computers that run Windows 10. All Microsoft Defender for Cloud Apps built-in anomaly detection policies are enabled.
Azure Environment
-
Litware has an Azure subscription linked to the litware.com Azure AD tenant. The subscription contains resources in the East US Azure region as shown in the following table.
Network Environment
-
Each Litware office connects directly to the internet and has a site-to-site VPN connection to the virtual networks in the Azure subscription.
On-premises Environment
-
The on-premises network contains the computers shown in the following table.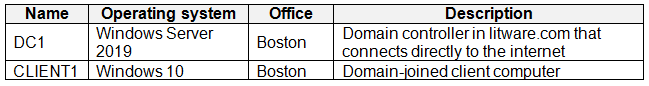
Current Problems
-
Microsoft Defender for Cloud Apps frequently generates false positive alerts when users connect to both offices simultaneously.
Planned Changes and Requirements
Planned Changes
-
Litware plans to implement the following changes:
•Create and configure Microsoft Sentinel in the Azure subscription.
•Validate Microsoft Sentinel functionality by using Azure AD test user accounts.
Business Requirements
-
Litware identifies the following business requirements:
•The principle of least privilege must be used whenever possible.
•Costs must be minimized, as long as all other requirements are met.
•Logs collected by Log Analytics must provide a full audit trail of user activities.
•All domain controllers must be protected by using Microsoft Defender for Identity.
Azure Information Protection Requirements
All files that have sensitivity labels and are stored on the Windows 10 computers must be available from the Azure Information Protection – Data discovery dashboard.
Microsoft Defender for Endpoint Requirements
All Microsoft Defender for Cloud Apps unsanctioned apps must be blocked on the Windows 10 computers by using Microsoft Defender for Endpoint.
Microsoft Defender for Cloud Apps Security Requirements
Microsoft Defender for Cloud Apps must identify whether a user connection is anomalous based on tenant-level data.
Microsoft Defender for Cloud Requirements
All servers must send logs to the same Log Analytics workspace.
Microsoft Sentinel Requirements
Litware must meet the following Microsoft Sentinel requirements:
•Integrate Microsoft Sentinel and Microsoft Defender for Cloud Apps.
•Ensure that a user named admin1 can configure Microsoft Sentinel playbooks.
•Create a Microsoft Sentinel analytics rule based on a custom query. The rule must automatically initiate the execution of a playbook.
•Add notes to events that represent data access from a specific IP address to provide the ability to reference the IP address when navigating through an investigation graph while hunting.
•Create a test rule that generates alerts when inbound access to Microsoft Office 365 by the Azure AD test user accounts is detected. Alerts generated by the rule must be grouped into individual incidents, with one incident per test user account.
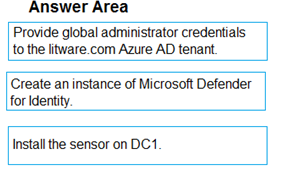
You need to configure DC1 to meet the business requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.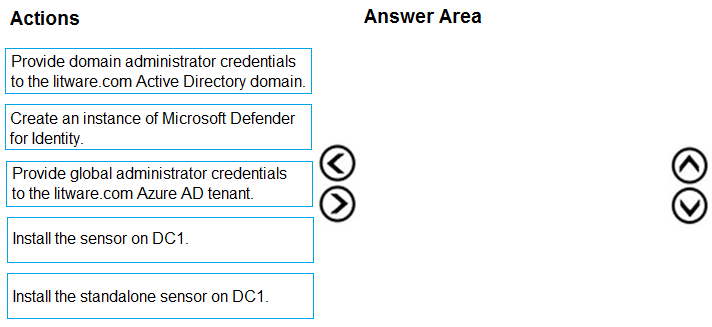
You have a Microsoft 365 subscription that uses Microsoft Purview and Microsoft Teams.
You have a team named Team1 that has a project named Project1.
You need to identify any Project1 files that were stored on the team site of Team1 between February 1, 2023, and February 10, 2023.
Which KQL query should you run?
- A. (c:c)(Project1)(date=(2023-02-01)..date=(2023-02-10))
- B. AuditLogs -
| where Timestamp between (datetime(2023-02-01)..datetime(2023-02-10))
| where FileName contains “Project1” - C. Project1(c:c)(date=2023-02-01..2023-02-10)
- D. AuditLogs -
| where Timestamp > ago(10d)
| where FileName contains “Project1”
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint.
You need to create a query that will link the AlertInfo, AlertEvidence, and DeviceLogonEvents tables. The solution must return all the rows in the tables.
Which operator should you use?
- A. search *
- B. union kind = inner
- C. join kind = inner
- D. evaluate hint.remote =
You have a Microsoft 365 E5 subscription that contains 100 Windows 10 devices.
You onboard the devices to Microsoft Defender 365.
You need to ensure that you can initiate remote shell connections to the onboarded devices from the Microsoft 365 Defender portal.
What should you do first?
- A. Modify the permissions for Microsoft 365 Defender.
- B. Create a device group.
- C. From Advanced features in the Endpoints settings of the Microsoft 365 Defender portal, enable automated investigation.
- D. Configure role-based access control (RBAC).
- « Previous
- Next »
Viewing page 11 out of 18 pages.
Viewing questions 51-55 out of 90 questions
Bạn có thể tham gia cộng đồng của chúng tôi bằng cách Join vào Group: https://www.facebook.com/groups/355742373099816
Hướng dẫn mua Dump demo
Bước 1: Thực hiện nhấn vào nút “MUA NGAY” và điền các thông tin cần thiết để đặt mua trực tiếp trên trang web.
Bước 2: Thực hiện thanh toán theo cú pháp: thanh toan don hang [mã
đơn hàng]
Xem hướng dẫn chi tiết cách thức thanh toán Tại đây
Sau khi thanh toán thành công vui lòng chờ trong vài phút để chúng tôi xác
nhận đơn hàng.
Sau đó bạn có thể quay lại có thể xem được toàn bộ Dump hoặc truy cập
vào mục Dump của tôi
Nếu trong vòng 15 phút bạn vẫn không xem được Dump vui lòng liên hệ qua
Chát trực tiếp trên website hoặc liên hệ qua Fanpage hoặc Zalo hoặc
Hotline của chúng tôi.




