Dump | demo: Dump Test Engine Demo miễn phí
You have an Azure subscription that contains a Log Analytics workspace.
You need to enable just-in-time (JIT) VM access and network detections for Azure resources.
Where should you enable Azure Defender?
- A. at the subscription level
- B. at the workspace level
- C. at the resource level
You use Azure Defender.
You have an Azure Storage account that contains sensitive information.
You need to run a PowerShell script if someone accesses the storage account from a suspicious IP address.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
- A. From Azure Security Center, enable workflow automation.
- B. Create an Azure logic app that has a manual trigger.
- C. Create an Azure logic app that has an Azure Security Center alert trigger.
- D. Create an Azure logic app that has an HTTP trigger.
- E. From Azure Active Directory (Azure AD), add an app registration.
HOTSPOT -
You manage the security posture of an Azure subscription that contains two virtual machines name vm1 and vm2.
The secure score in Azure Security Center is shown in the Security Center exhibit. (Click the Security Center tab.)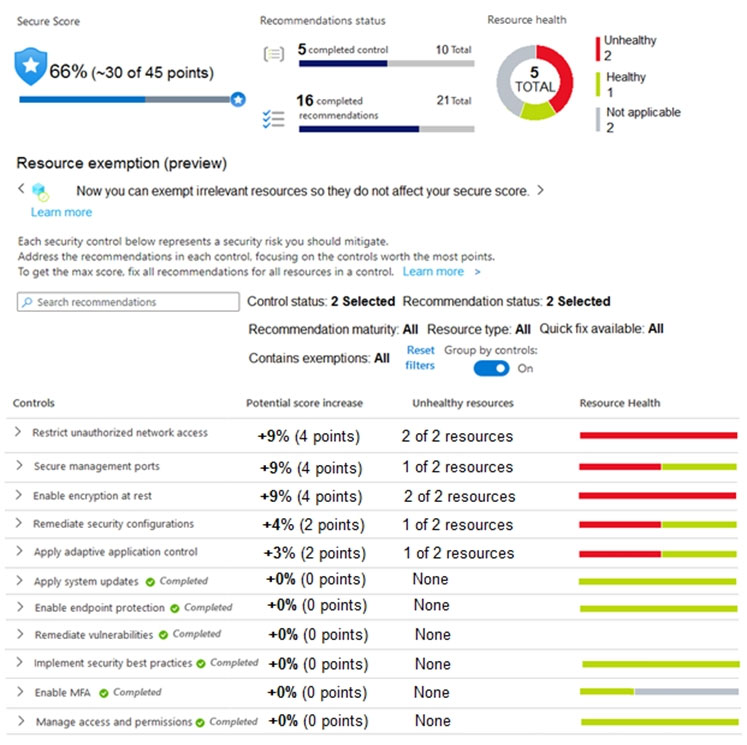
Azure Policy assignments are configured as shown in the Policies exhibit. (Click the Policies tab.)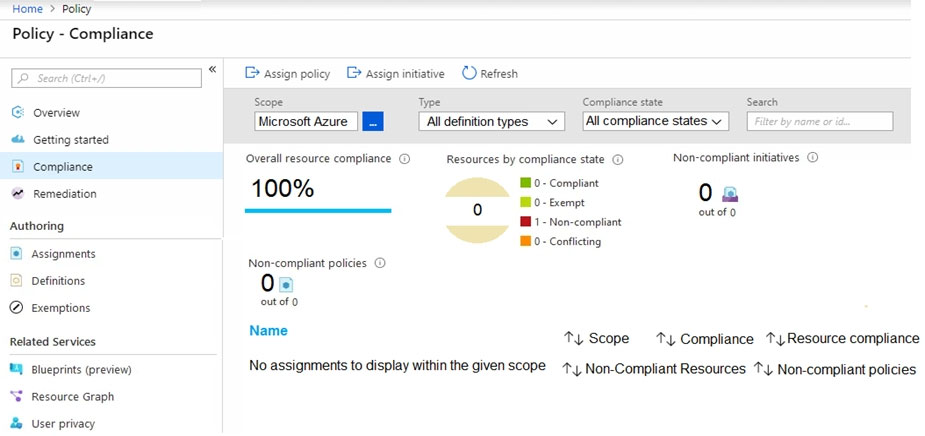
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area: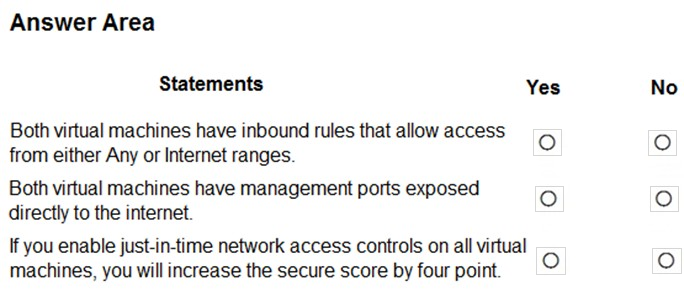
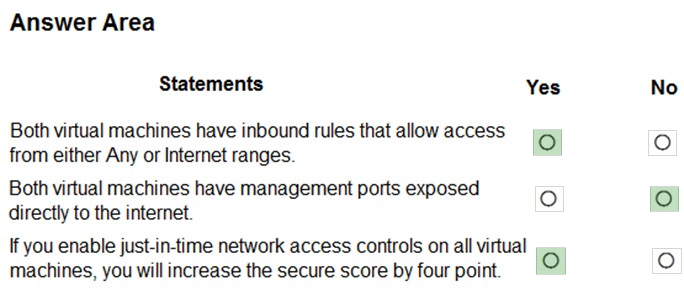
https://techcommunity.microsoft.com/t5/azure-security-center/security-control-restrict-unauthorized-network-access/ba-p/1593833 https://techcommunity.microsoft.com/t5/azure-security-center/security-control-secure-management-ports/ba-p/1505770
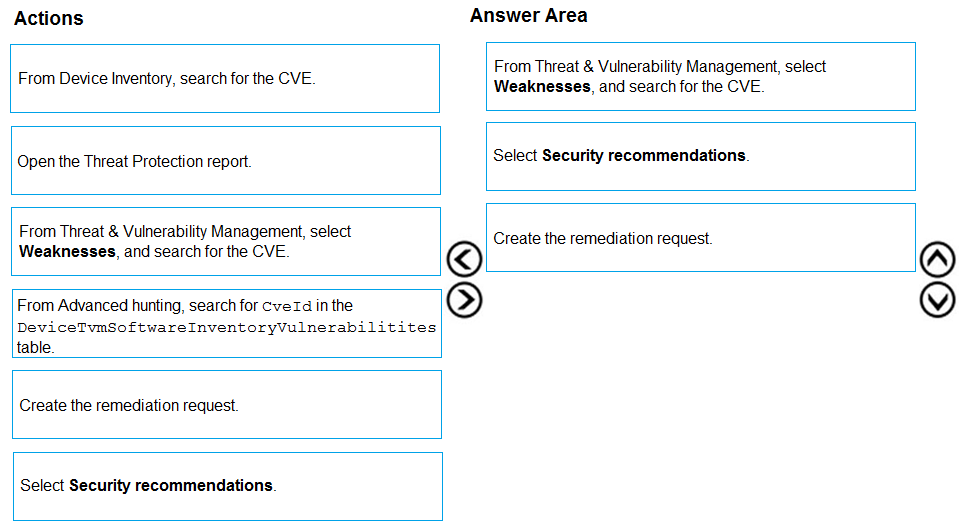
DRAG DROP -
You are informed of a new common vulnerabilities and exposures (CVE) vulnerability that affects your environment.
You need to use Microsoft Defender Security Center to request remediation from the team responsible for the affected systems if there is a documented active exploit available.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place: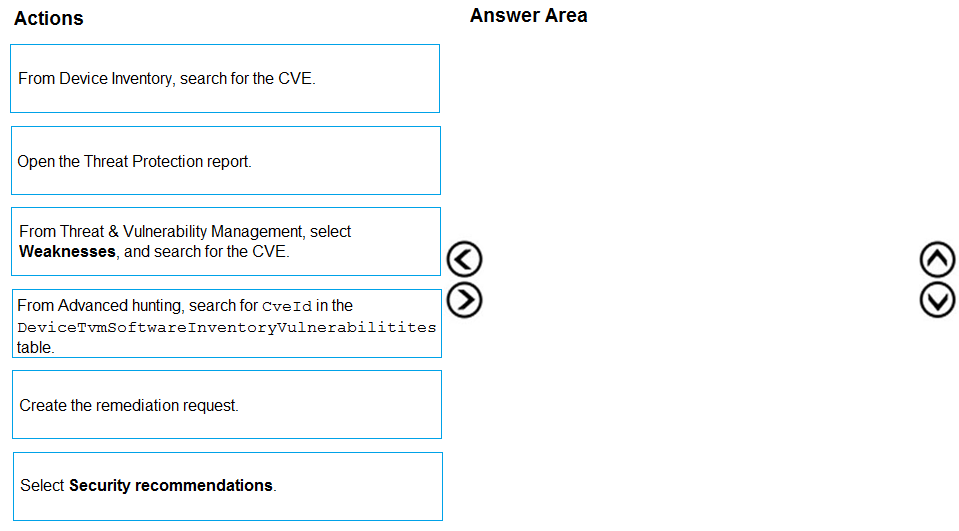
https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/microsoft-defender-atp-remediate-apps-using-mem/ba-p/1599271
You use Azure Security Center.
You receive a security alert in Security Center.
You need to view recommendations to resolve the alert in Security Center.
What should you do?
- A. From Security alerts, select the alert, select Take Action, and then expand the Prevent future attacks section.
- B. From Security alerts, select Take Action, and then expand the Mitigate the threat section.
- C. From Regulatory compliance, download the report.
- D. From Recommendations, download the CSV report.
- « Previous
- Next »
Viewing page 17 out of 18 pages.
Viewing questions 81-85 out of 90 questions
Bạn có thể tham gia cộng đồng của chúng tôi bằng cách Join vào Group: https://www.facebook.com/groups/355742373099816
Hướng dẫn mua Dump demo
Bước 1: Thực hiện nhấn vào nút “MUA NGAY” và điền các thông tin cần thiết để đặt mua trực tiếp trên trang web.
Bước 2: Thực hiện thanh toán theo cú pháp: thanh toan don hang [mã
đơn hàng]
Xem hướng dẫn chi tiết cách thức thanh toán Tại đây
Sau khi thanh toán thành công vui lòng chờ trong vài phút để chúng tôi xác
nhận đơn hàng.
Sau đó bạn có thể quay lại có thể xem được toàn bộ Dump hoặc truy cập
vào mục Dump của tôi
Nếu trong vòng 15 phút bạn vẫn không xem được Dump vui lòng liên hệ qua
Chát trực tiếp trên website hoặc liên hệ qua Fanpage hoặc Zalo hoặc
Hotline của chúng tôi.




